
Essential Protocols for Operations Managers

Your phone buzzes at 3 AM. The AI-powered recommendation engine is producing bizarre product suggestions—winter coats for customers in Arizona, baby products for retirees. Customer support is flooded with complaints. Revenue is dropping in real-time.
What's your call? Shut down immediately and lose overnight revenue? Investigate while the system runs and risk further damage? Roll back to yesterday's version without knowing what broke?
This lesson equips you with a battle-tested framework to handle AI incidents with confidence—minimize damage, protect your organization's reputation, and restore operations efficiently.
AI incidents surged 30% in 2024 (OECD data). As an operations manager, you're the first responder. This playbook reduces response time by 40%, limits business impact, and protects your reputation when seconds count.
An AI incident is any event where an AI system behaves unexpectedly, produces harmful outputs, or fails to meet operational requirements, potentially causing harm to users, the business, or stakeholders.
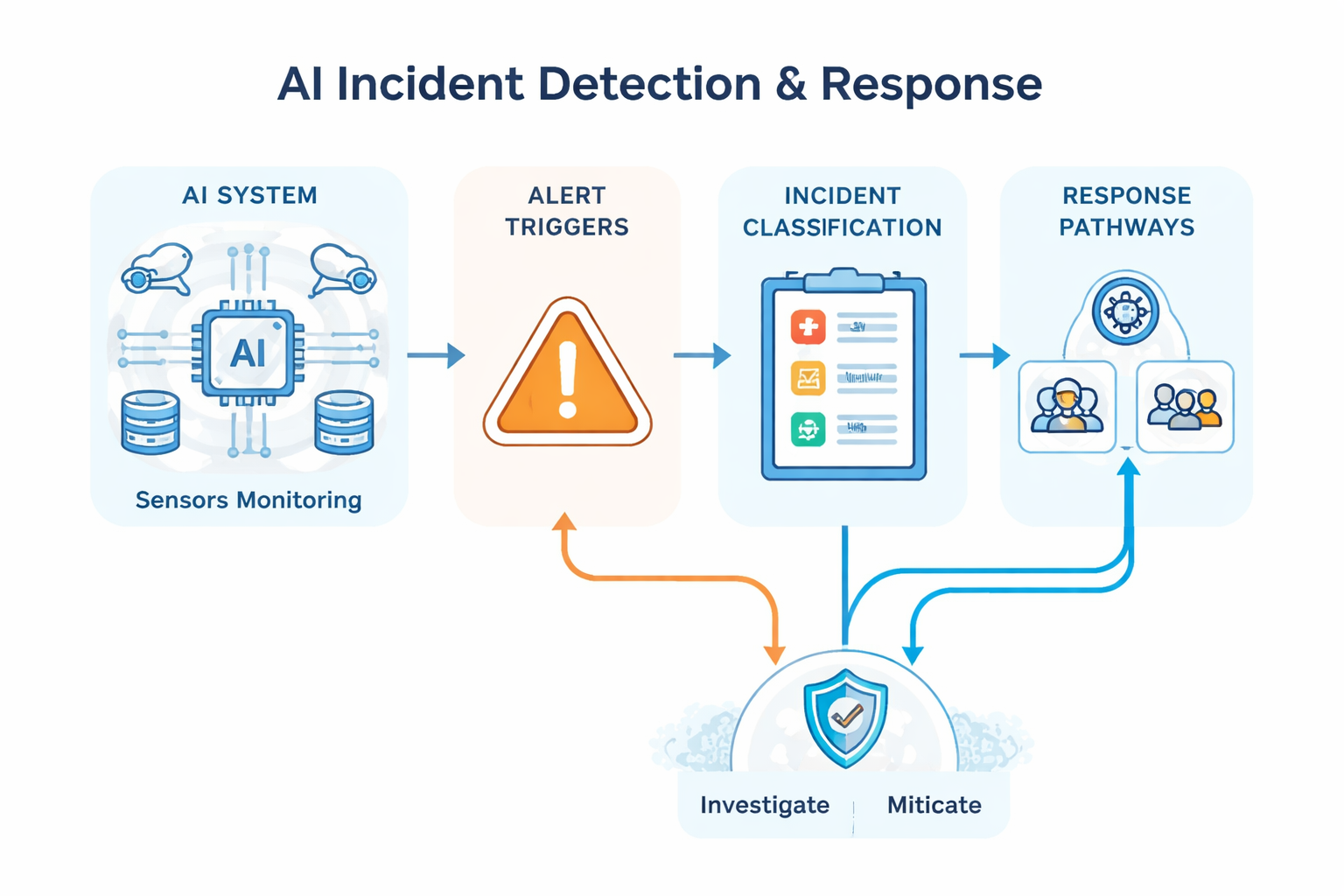
Adapted from NIST AI Risk Management Framework, this playbook organizes incident response into four actionable phases:
Recognize anomalies through monitoring, alerts, and user reports. Classify severity and scope quickly.
Limit the incident's impact. Isolate affected systems, pause deployments, or roll back to stable versions.
Diagnose root cause, apply fixes, and restore services. Communicate with stakeholders throughout.
Document lessons learned, update playbooks, and implement preventive measures to reduce future risk.
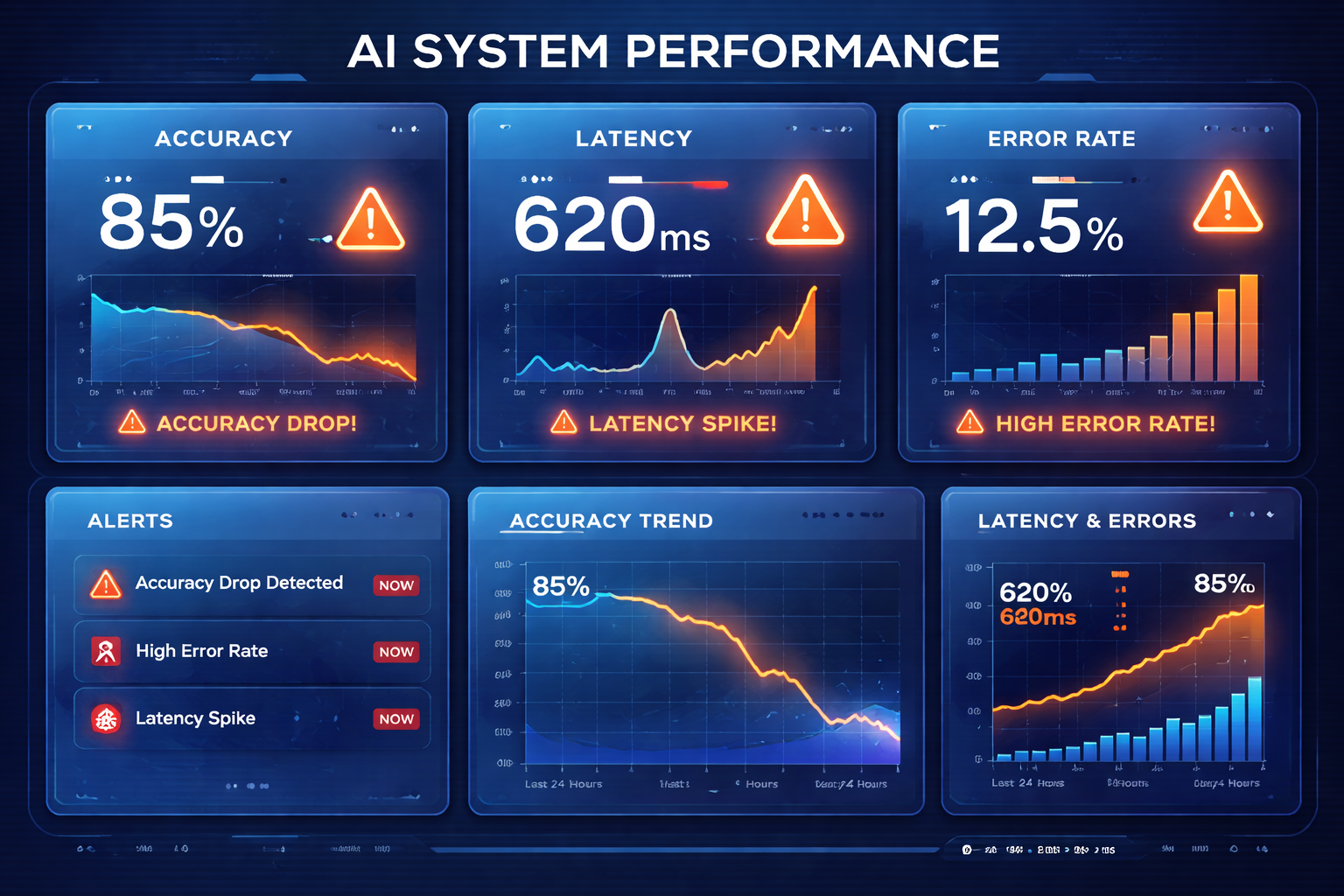
Effective detection relies on continuous monitoring across multiple dimensions. Implement automated alerts for:
The goal of containment is to stop the bleeding. Your response depends on incident severity and business impact:

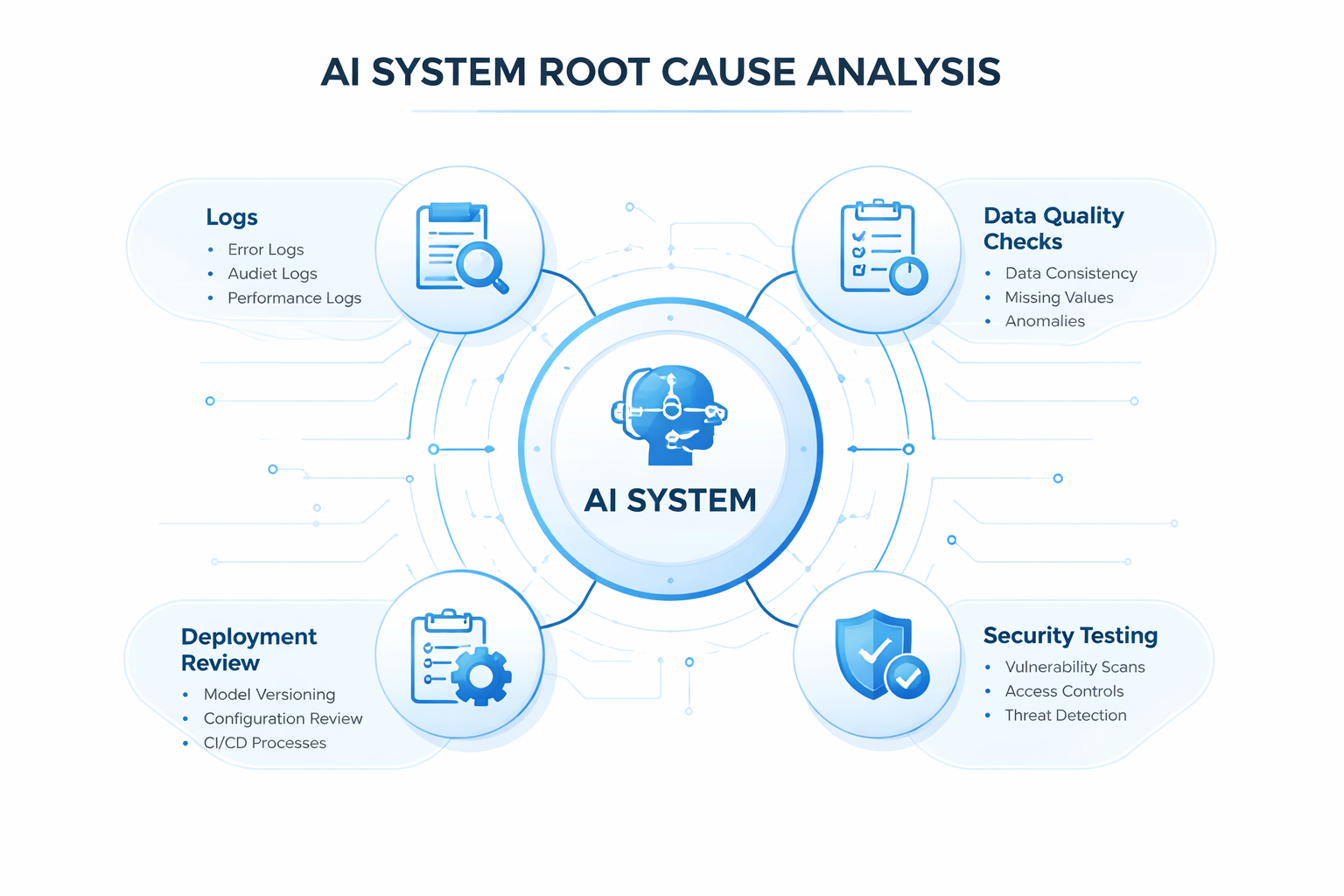
Once contained, conduct a systematic investigation to identify why the incident occurred:
Validate fixes in staging before production deployment. Gradually restore service with enhanced monitoring.

Within 48 hours of resolution, gather the incident response team for a structured review. Focus on learning, not blame.
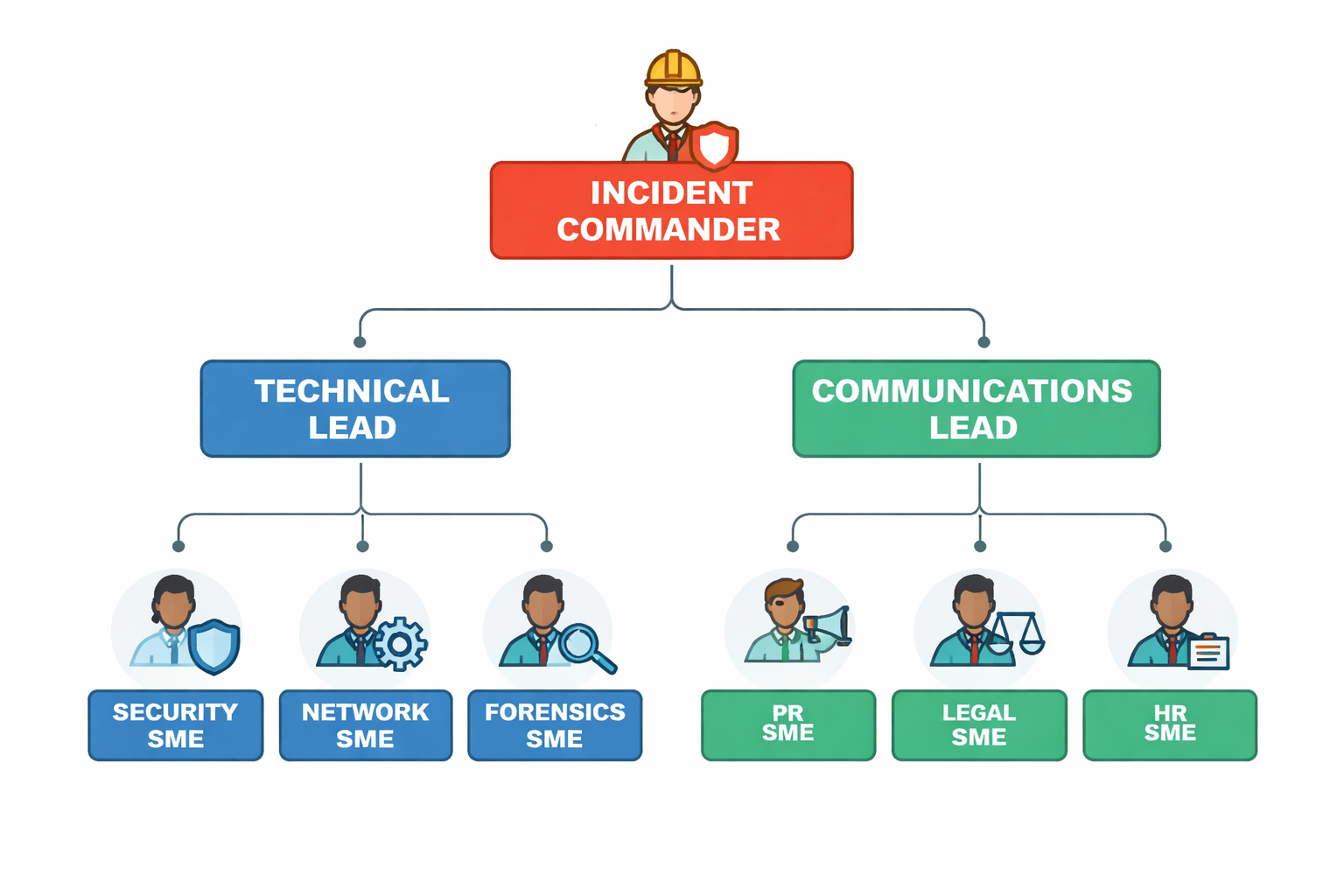
Assign clear roles and responsibilities before incidents occur:

The best incident response is prevention. Integrate these practices into your AI operations:
Track performance, data quality, fairness metrics, and security indicators continuously with automated alerting.
Implement pre-deployment validation, stress testing, adversarial testing, and canary releases to catch issues early.
Establish AI governance committees, maintain system inventories, and enforce approval workflows for changes.
Conduct periodic reviews of model performance, bias assessments, security scans, and compliance checks.
Foster a culture where team members feel empowered to raise concerns, report anomalies, and challenge assumptions. Psychological safety accelerates detection and improves response quality.
You've learned a structured, proven framework to manage AI incidents with confidence. Here are the essential points to remember:
Monitor continuously. Detect anomalies early. Classify severity quickly to match response urgency.
Stop the bleeding with graceful degradation, rollbacks, or feature flags. Balance business continuity with risk.
Conduct root cause analysis. Apply targeted fixes. Validate before production. Communicate transparently.
Hold blameless retrospectives. Update playbooks. Implement preventive measures. Track improvement metrics.
Invest in monitoring, testing, governance, and culture. Prevention beats response every time.
Assign roles. Document escalation paths. Practice with simulations. Make incident response muscle memory.
You've completed the tutorial. Now demonstrate your understanding of AI incident response protocols.